Adding more RAM to a computer system is not always a silver bullet that will just automatically make it faster and or increase performance.
‘For the most part, increasing RAM capacity alone does not actually speed up your computer, rather, it prevents it from slowing down’ – Reasonable IT
Don’t believe us? Check out this recent, real world scenario testing on a system between 8GB and 16GB. We covered some simple real world scenarios most people would quantify as computer performance, such as, app start up time, system boot time, video rendering time and gaming fps. The entire point of this video was to prove by demonstration that simply increasing ram capacity from 8GB to 16GB on a system that was not previously experiencing RAM over-utilization, leads to no discernible difference in system performance.
Increasing RAM capacity in a computer is often hailed as a solution to boost performance. We’re here today to help you make an informed decision and not waste time or money on increasing your systems memory when it may very well not be the best upgrade path for you. But then why does adding more RAM not always lead to a faster system? Let’s explore this idea further ->
Understanding RAM Bottlenecks
Before rushing to upgrade RAM, it’s crucial to evaluate whether your system actually requires additional memory. RAM, or Random Access Memory, serves as a temporary storage for active programs and processes. When your system runs out of available RAM, it resorts to slower storage devices, causing performance slowdowns. This scenario is known as a RAM bottleneck and in most cases, if your computer isn’t experiencing a RAM bottleneck, increasing RAM capacity may not yield significant improvements.
So How Will I Know If I Have A RAM Bottleneck On My System?
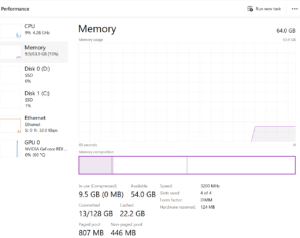
Identifying bottlenecks in your system falls outside the scope of this blog but in short, you’ll want to monitor the memory usage of your system with performance monitoring tools such as Task Manager or Performance Monitor (which are built into Windows OS). These tools display metrics such as total RAM usage, available RAM, and memory usage by individual processes.
If you consistently observe high levels of RAM usage close to or at maximum capacity, accompanied by performance degradation such as slow application responsiveness or frequent disk swapping, it may indicate that your system is experiencing RAM bottlenecks. In such cases, increasing your system’s RAM capacity can significantly improve performance. However, it’s important to note that the increase in speed will only bring your PC back up to its expected performance level, rather than exceeding it.
The Law of Diminishing Returns
Remember, once your system has enough RAM to handle its workload efficiently, further increases in capacity may offer diminishing returns (if any at all) in terms of performance enhancement. If you are not experiencing a RAM bottle neck but still desire increased system performance, consider investing in other hardware upgrades (such as an SSD/faster SSD) or optimizing software configurations for better value.
Conclusion
While increasing RAM capacity can enhance system performance under genuine memory shortages, it’s important to recognize that it’s not a one-size-fits-all solution. Before investing in a RAM upgrade, carefully evaluate your system’s requirements and identify potential bottlenecks. Adopting a holistic approach to system optimization, considering factors beyond just RAM capacity, is crucial for achieving optimal performance and efficiency.
#will adding more ram to my computer really make it faster?
#should i add more ram to my computer?
#does increasing ram really make my computer faster?